This challenge focuses on desktop application security, and I’ll do my best to explain in as-layman-as-possible terms what’s going on in each step, however some basic knowledge of the following might help you you in completing this challenge:
- Debuggers
- x86 ASM
For this task, we will need a copy of Windows (running in a VM is fine) and a debugger. I suggest the program x64dbg, which we can download for free here
Our first step is to download and unzip the challenge archive, the password is ‘hackthebox’. Once you’ve extracted the EXE, open x32dbg.exe from the x64dbg package. In the x64dbg window, go to File > Open and select the testing executable we extracted. The windows should now look a little bit like this:
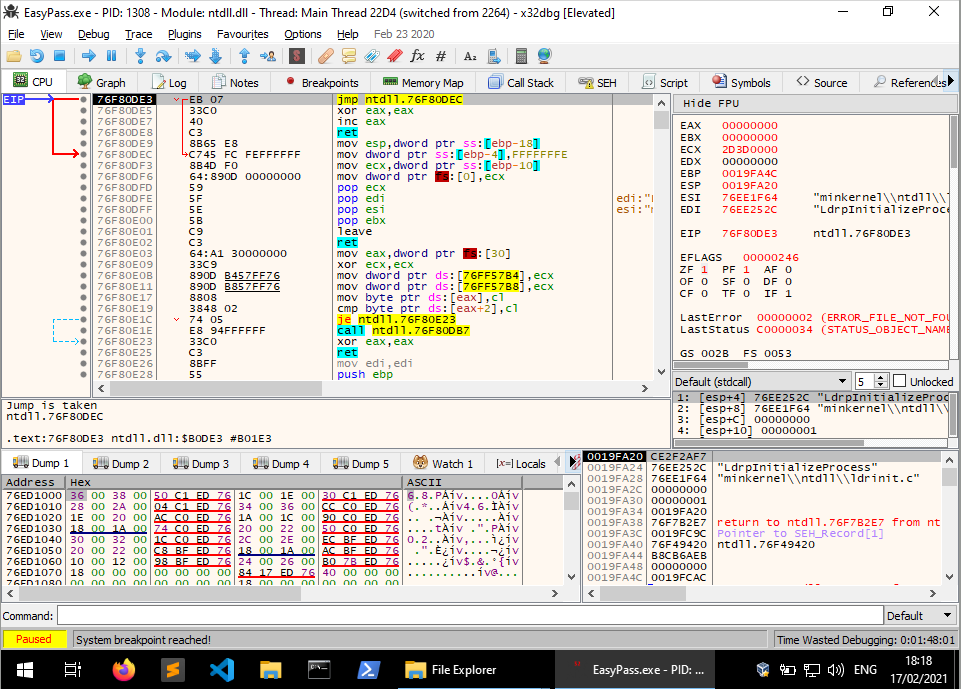
This will look like a lot of nonsense to someone just starting out in reverse engineering, but don’t worry! we won’t be worrying about these just yet. For now, click the Right Arrow next to the pause button once to get to the application’s entry point (where the Operating System’s code loading processes stop and the actual application begins), and again to run the actual program. The program then asks for a password:
Entering a bunch of rubbish into the password field gives us the following message:
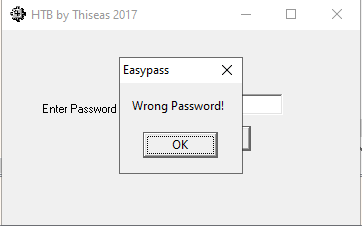
This, at first, may not seem useful, but take a copy of the message it has just given us, go back into the debugger and press Ctrl + F2 to restart the application. Now enter a tab called References and look for a search bar at the bottom. Put the message text into this box, and you should see this:
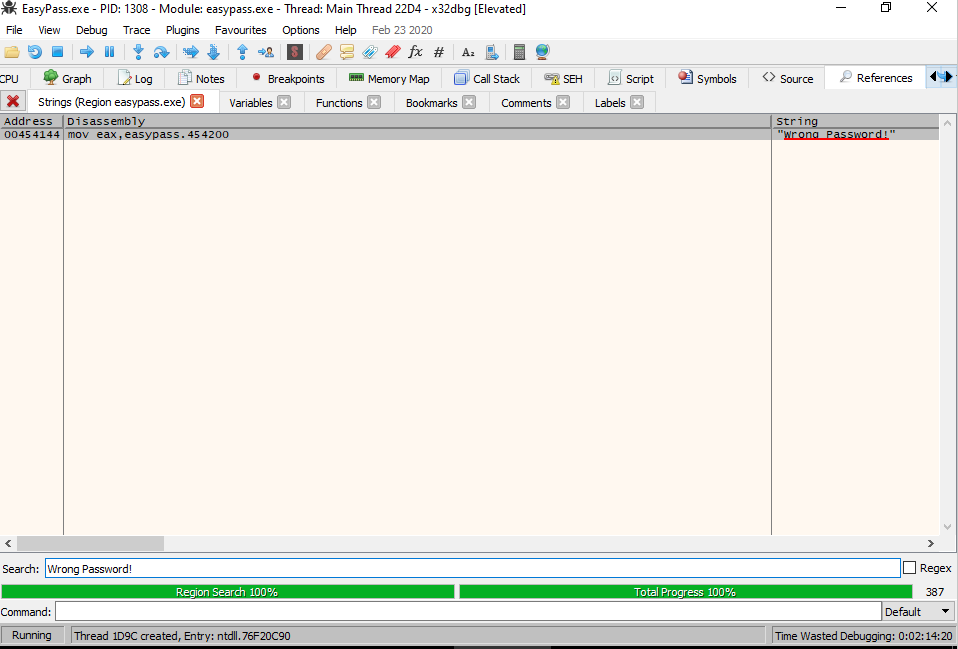
The entry we see here is telling us where in memory the string is being used. If we double click it, it will take us to that area in the CPU instruction stack.
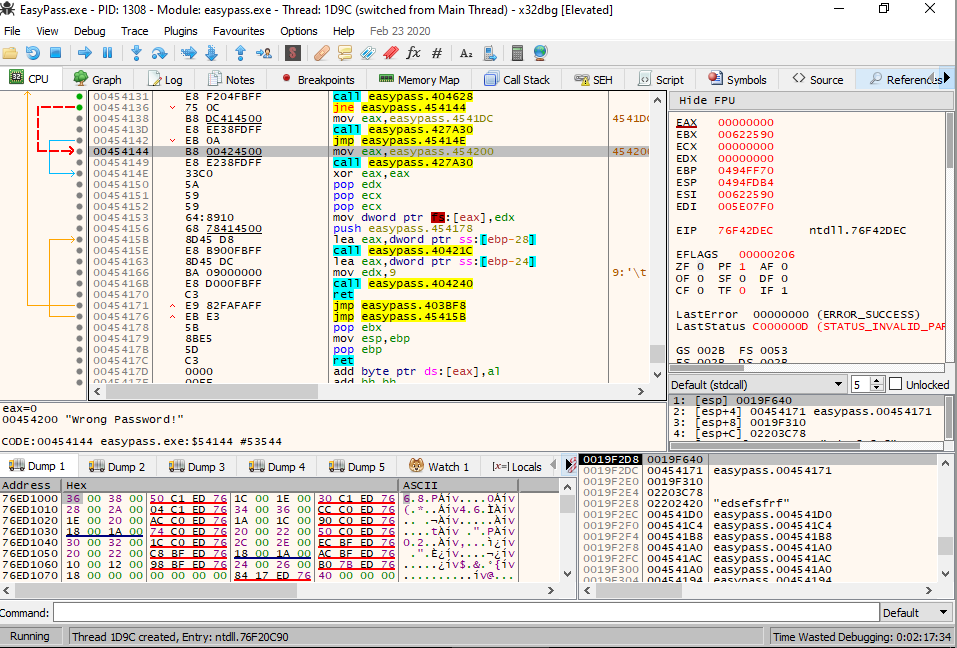
Let’s take a look at the red arrow, where it starts from and the instruction before it:
call easypass.404628
jne easypass.454144This code is doing the following:
- calling a function within the binary, likely comparing two values (the
callinstruction) - comparing the two values to see if they’re equal. If they are not, skip to another part of the code (the
jneinstruction)
What we’re going to do is insert what is known as a breakpoint at the call instruction. This will stop the executable from running once it reaches that instruction. We can then step through the code instruction by instruction. Look at the register values (top right corner of the window) while we do this. Let’s run the application again, and once again put gobbledegook in the password field.
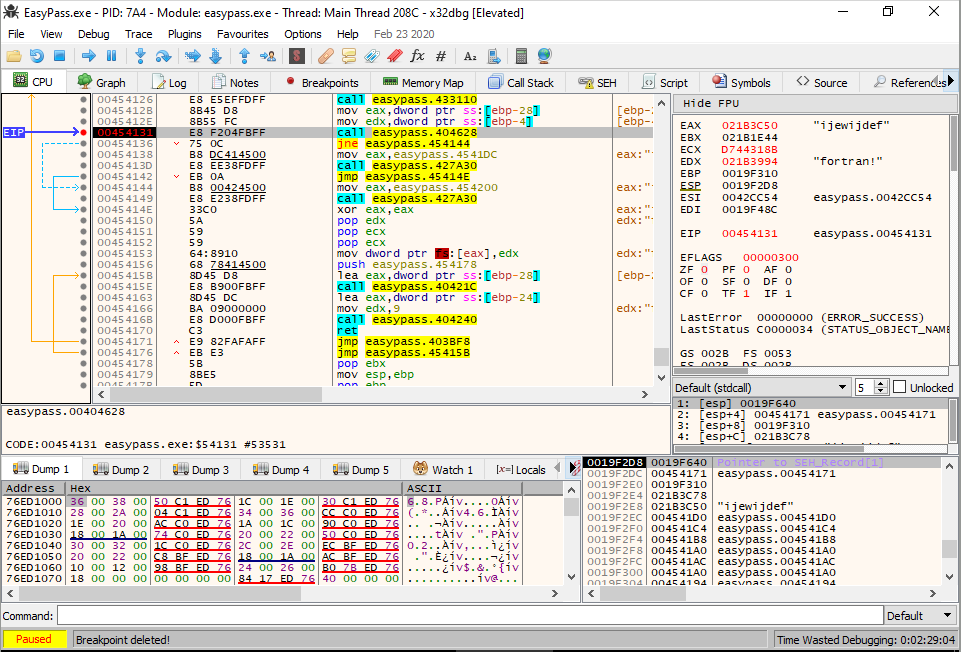
The value in the EAX register is our gobbledegook password, but the value in the EDX register is a little more interesting…Note it down and restart the program, entering this new value into the program.
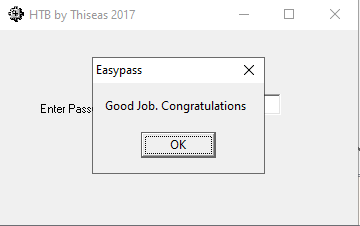
Success! We have cracked the application.
